Which Statements Are True Regarding Secure File Transfer Protocol
SSH encrypts files during the file transfer process. An attacker who gains access to SSH encryption keys can decrypt and read content.

What Is File Transfer Protocol Ftp And How Does It Work
They are encapsulated within UDP datagrams.
/filezilla-cb091304cca54cf0b494cfa02aba0e7d.jpg)
. Which of the following statements is true regarding the destination VPN connection name. These four header fields are each two bytes long. A Client-server b P2P c Data centric d Service oriented Identify the incorrect statement regarding FTP.
They guarantee datagram delivery. They can provide hosts with information about network problems. DNS makes use of UDP.
SSH and SFTP were designed by the Internet Engineering Task Force IETF for greater web security. So there are two false answers. Secure File Transfer Protocol SFTP is a file protocol for transferring large files over the web.
Of the 3 options above E is not SECURE so it does not meet the full brief leaving us with just C D. A Fine Transfer Protocol b File Transfer Protocol c First Transfer Protocol d Fast Transfer Protocol FTP is built on _____ architecture. You can use SSH with FTP.
Because it is fast and has a low overhead UDP is preferred. QUESTION 31 Which of the following statements are true about network protocols. It is faster than SCP but platform dependent.
Which of the following statements is NOT true of Secure Shell SSH. Which of the following statements is NOT true of Secure Shell SSH. Which of the following statements is true.
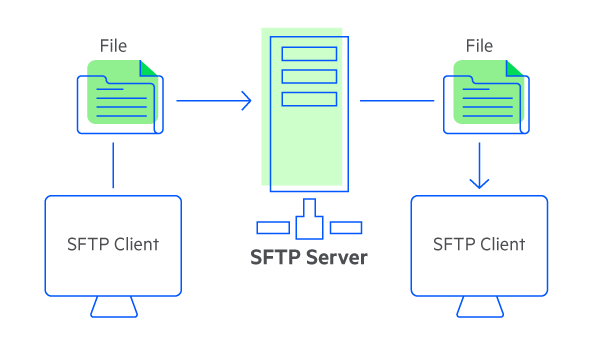
SFTP SSH FTP or Secure FTP encrypts commands and data uses SSH for transferring files and typically runs on TCP port 22. Only the data is encrypted not the commands. Which of the following statements is correct.
TCPIP controls web browsers that access the web. RRQ is a read request message which is used to establish the connection between client and server for reading data. The Transmission Control Protocol Internet Protocol TCPIP would make use of the protocol.
Which statements are true regarding Secure File Transfer Protocol SFTP. FTP is a good alternative to sending an e-mail attachment. TCPIP is used to transfer text files programs spreadsheets and databases across the Internet.
You are configuring a VPN client on a Windows 2016 server using IPsec to create a secure tunnel to a L2TPIPsec server. A new hash will be created for the authentication header AH. An attacker who gains access to SSH encryption keys cannot decrypt and read content.
Group of answer choices. An attacker who gains access to SSH encryption keys cannot decrypt and read content. True DNS queries are served using the User Datagram Protocol UDP on port 53.
A hash will not remain the same if the bytes change on transfer. This is a UDP protocol which allows us to send to multiple clients at once. Which of the following statements about File Transfer Protocol FTP is true.
They acknowledge receipt of a TCP segment. The VPN name may be dictated by your organizations naming conventions. It is slower than SCP but platform independent.
A FTP stands for File Transfer Protocol b FTP uses two parallel TCP connections. Which of the following statements is TRUE regarding the network protocol which makes use of the File Transfer Protocol FTP protocol. Question 8 Which of the following statements is true regarding the destination from ISOL 532 at University of the Cumberlands.
It is also called SSH File Transfer Protocol. You should know that the IPSec protocol would make use of the File Transfer Protocol TTP protocol. The only statement that is true is that the authentication information is a keyed hash that is based on all the bytes in the packet.
Secure Shell is a cryptographic component of internet security. L2TP works only for IP networks not non-IP networks. E- Trivial File Transfer Protocol TFTP.
SSH encrypts files during the file transfer process. The VPN name should be redundant not unique in your Network and Sharing Center. The VPN name may be dictated by your organizations naming conventions.
File Transfer Protocol Defined. TCPIP is the document format used to produce web pages. True The UDP header is always 8 bytes long.
Internet resources can be used for a variety of purposes beyond the World Wide Web and e-mail. TCPIP is the basic protocol that permits communication between Internet sites. It builds on the File Transfer Protocol FTP and includes Secure Shell SSH security components.
Network protocols define the content of the information carried in the body of the packet. FTPS also known as FTP Secure and FTP-SSL is common for web servers having SSL. They are encapsulated within IP datagrams.
File Transport Protocol or FTP is an open protocol standard that is widely used to transport and receive large filesIt can. You can use SSH with FTP. Which statements are true regarding ICMP packets.
It is not true that It always runs on TCP port 22. There are five messages of TFTP that are RRQ WRQ DATA ACK ERROR. Network protocols define the kind of information that can be legally stored on a web site.
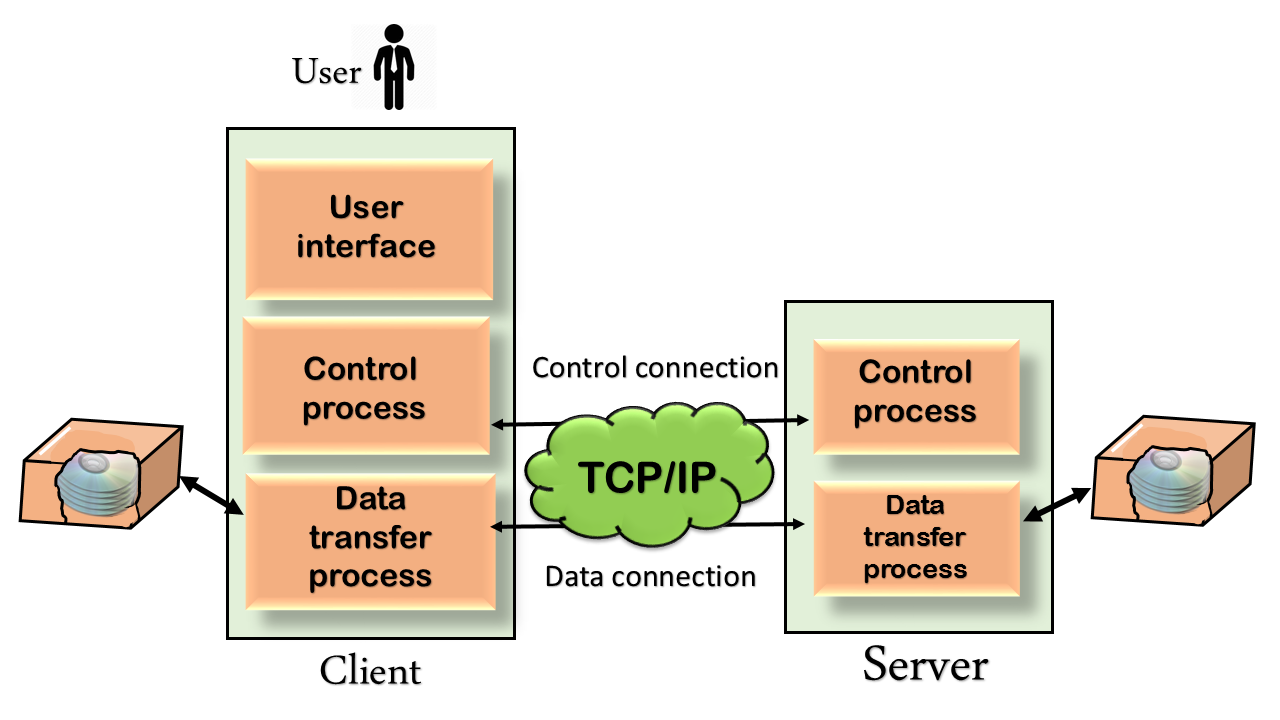
Network protocols for the Internet comprise a stack of three layers where each. D- Secure Copy Protocol SCP is a secure file-transfer facility based on SSH and Remote Copy Protocol RCP. L2TP does not perform encryption.
Comment SFTP is NOT FTP over SSL -- FTPS is FTP over SSL. WWQ is a write request message used to establish. An attacker who gains access to SSH encryption keys can decrypt and read content.
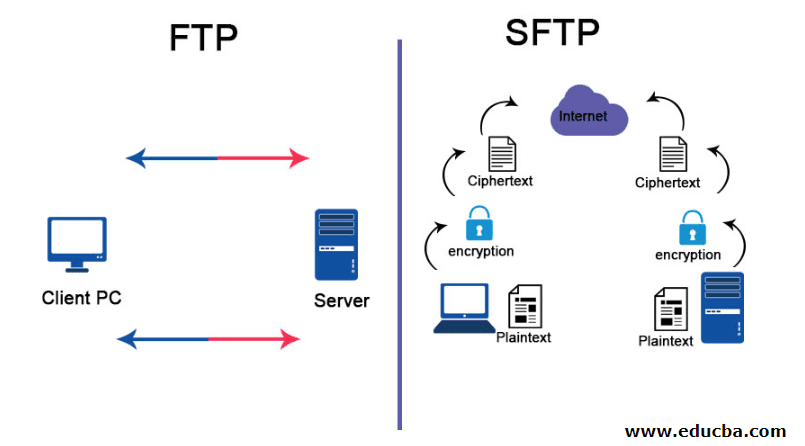
Sftp Ftp To Snowflake 2 Easy Methods

Sftp Ftp To Snowflake 2 Easy Methods

File Transfer Protocol Overview Uses What Is Ftp Video Lesson Transcript Study Com

What Is Sftp Secure File Transfer Protocol Port Number
/filezilla-cb091304cca54cf0b494cfa02aba0e7d.jpg)
File Transfer Protocol Ftp Definition

5 Secure File Transfer Solutions That Are Better Than Ftp
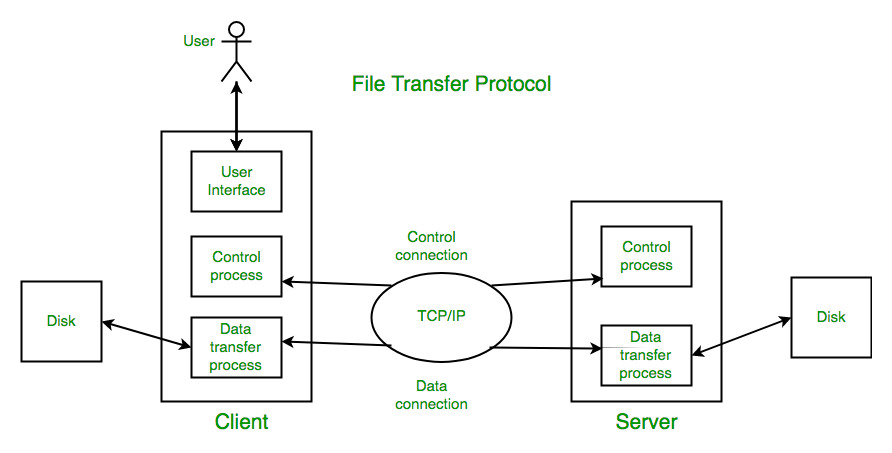
File Transfer Protocol Ftp In Application Layer Geeksforgeeks

What Is The Advantage Of A File Transfer Protocol Advantage Public Network Network Sharing

Corporate To Bank Connectivity In Sap An Overview Sap Blogs

Secure Ftp Which Is The Better Protocol Sftp Vs Ftps

What Is Secure File Transfer Protocol Sftp Definition From Techopedia

Difference Between Ftp And Smtp Webeduclick
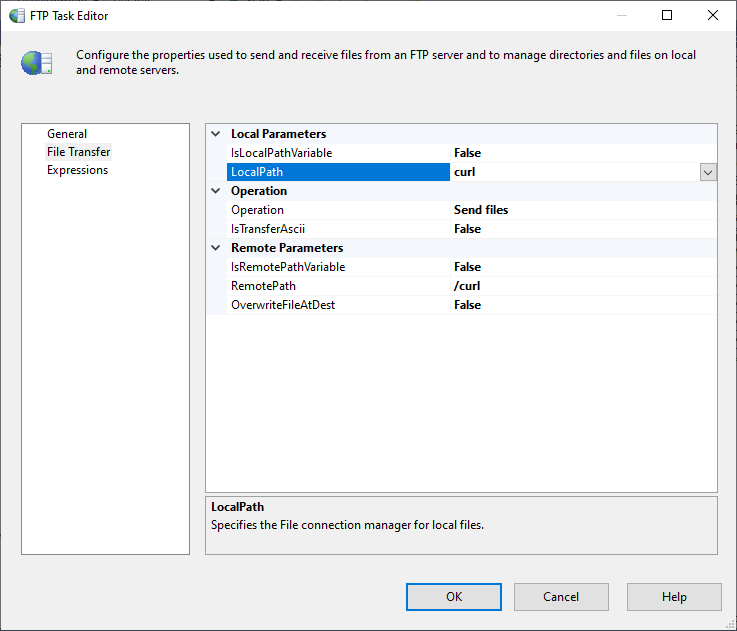
An Overview Of The Ssis Ftp Task
:max_bytes(150000):strip_icc()/filezilla-cb091304cca54cf0b494cfa02aba0e7d.jpg)
File Transfer Protocol Ftp Definition

What Is Sftp Secure File Transfer Protocol Port Number
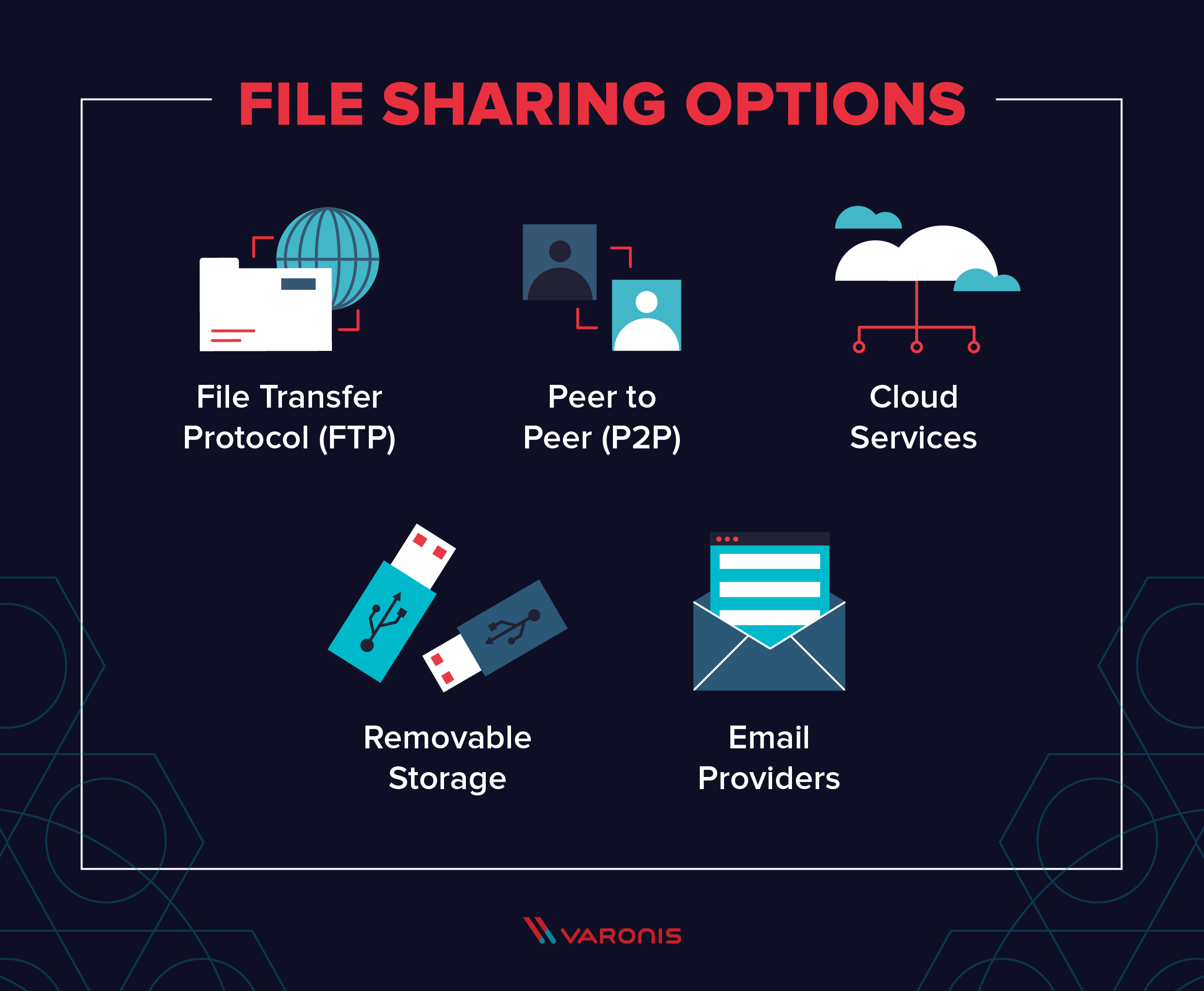
10 Secure File Sharing Options Tips And Solutions
/filezilla-cb091304cca54cf0b494cfa02aba0e7d.jpg)
Comments
Post a Comment